Say Hello to Maggie, the Latest in SQL Server Malware
Author: Jeff Duncan | 6 min read | October 11, 2022
Let us introduce you to Maggie. Maggie is your new nightmare. Maggie is a malicious backdoor malware designed for SQL Server, recently discovered by DCSO CyTec. Let’s take a look at how Maggie works and what you can do to protect your databases.
As of this writing, out of 600,000 servers scanned worldwide by DCSO CyTec, Maggie has been found on 285 servers in over 42 countries. The geographic focus is primarily focused around South Korea, India, Vietnam, China, and Taiwan.
What is the SQL Server Malware Maggie?
Maggie is malware that is an Extended Stored Procedure DLL, which is a special extension used by Microsoft SQL Servers that allow it to do work inside and outside of SQL. It is controlled by SQL queries to perform many operations, such as brute-force logins to other MS SQL servers. So far, it has only been found in the Asia-Pacific region.
Antivirus detected it as APT_ShadowForce_Malware_ON_Nov17_1 and Trojan/Win.ShadowForce.R472810. The DLL is signed by DEEPSoft Co., Ltd. and has a single export called maggie.
An extended stored procedure is the method SQL Server uses to interact outside of SQL Server. The most well-known example of this is xp_cmdshell, which is the built-in extended procedure that allows cmd line to interact with the server from queries inside of the MSSQL Server.
Maggie is an extended procedure that is actually a fully functional backdoor controlled by SQL queries. The attacker must have access in SQL to load the MAGGIE ESP into the server.
What Can Maggie Do Once It Has Access to SQL Server?
DCSO CyTec and other security researchers are unsure how the actual Maggie attacks are performed in real-world environments as of this writing. However, once Maggie is installed, it offers wide access to a broad number of commands. Here is the list of commands currently identified by DCSO CyTec:
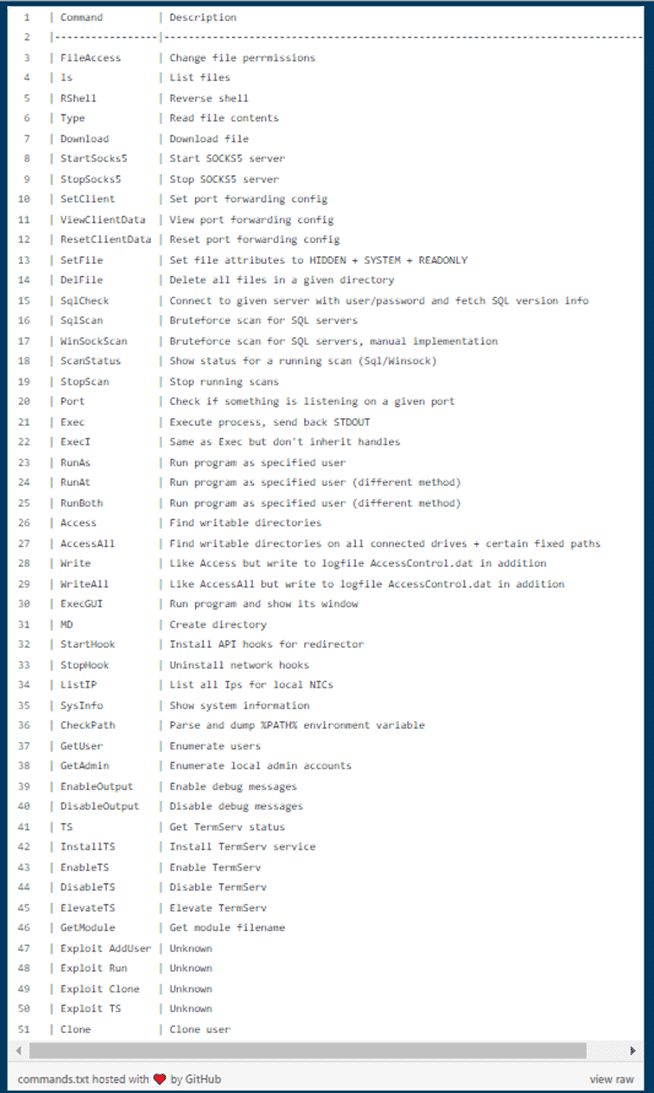
The Maggie malware also includes network bridge functions. These make it possible to redirect ports that SQL listens on and allows for intercepted communications.
At Datavail, we strive to keep on top of security issues so that we can protect our customers as quickly as possible. We also want to let our general audience know so that the issue does not spread.
What Can You Do to Protect SQL Servers From Maggie?
First, make sure that you keep your Antivirus and Malware protection programs up-to-date with the latest updates. While this seems obvious, many people delay doing updates for various reasons. One of these may be a Change Control policy. You should consider these types of updates as an urgent priority.
Second, you need to have proper security audits. This backdoor takes advantage of accounts that have sysadmin and local admin access. You need to strive to give each account in any system the Least Privilege it can have and still function properly.
We all know the easiest thing to do is to give a database user full access to simplify life. But doing this opens all kinds of loopholes that an exploit like Maggie can take advantage of. You should do regular security audits and make sure you limit the number of accounts that have full access.
Also, if these are SQL Server authenticated database users, you should make sure they follow a strict policy like your Windows Domain accounts do. Make sure the passwords are not easy to Brute Force attack. Believe it or not, the passwords like Password1, password123 etc. are very easy to identify.
Third, but far from final, we all need to be aware. Most of our businesses have a security department. But we cannot relax or rest assured that they will foresee and find everything. We all need to be the eyes and ears for threats.
Even here at Datavail, a database administrator found the details out about Maggie and brought it to the attention of our Chief Information Security Officer. It is all of our duties to be vigilant, protect ourselves, and keep up with security concerns. None of us want to see OUR company as the next company that was a victim to a major attack.
Lastly, if your organization needs help assessing the danger to your SQL Server databases, Datavail’s SQL Server experts are available to help you mitigate risks from this new vulnerability. Contact us and we’ll be glad to help.
